A flow chart of the generic AES-256 algorithm steps for encryption and... | Download Scientific Diagram

Comparison of time taken for various methods of AES key generation and... | Download Scientific Diagram
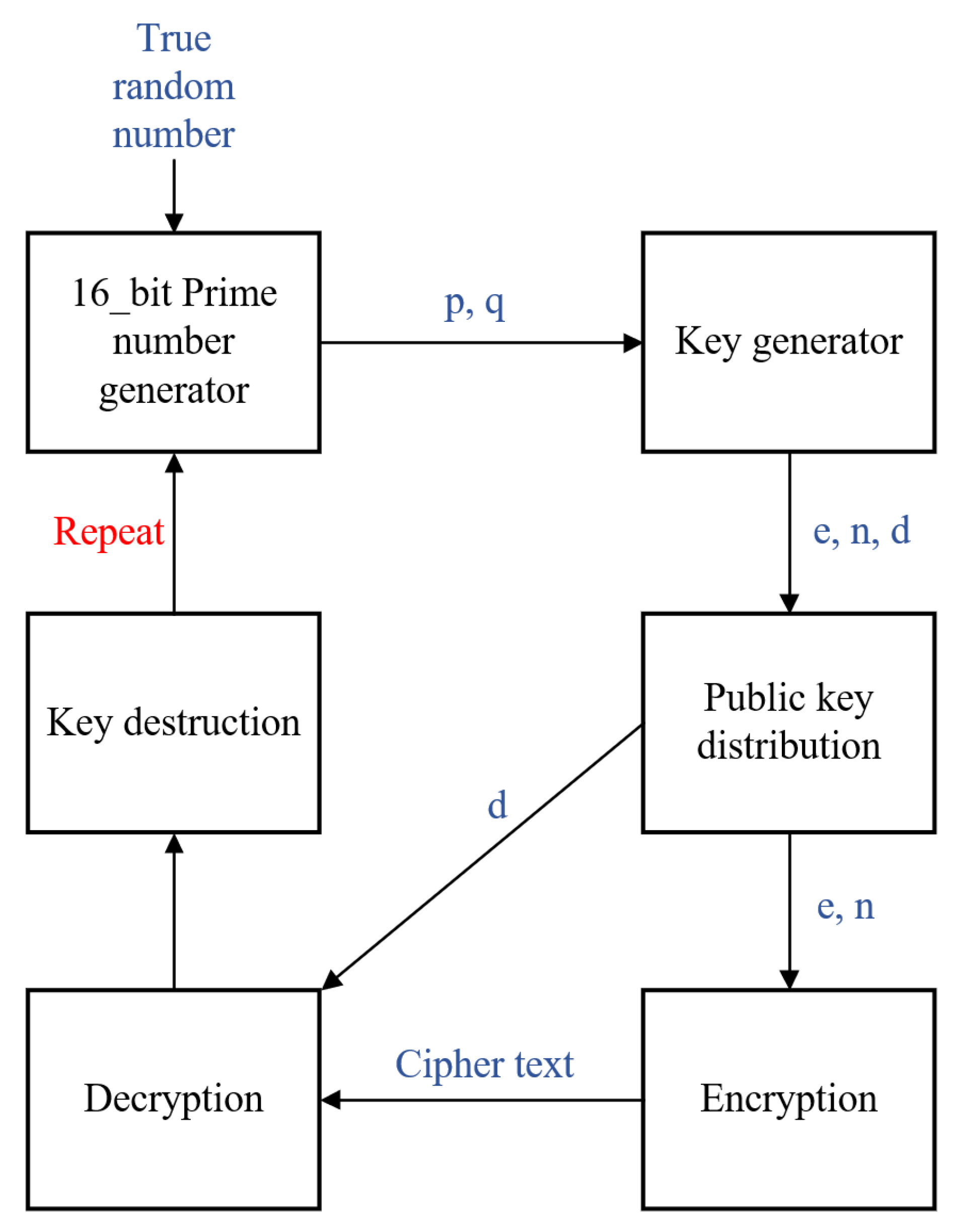
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices

Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)
![Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key generation and parallel computing for RGB image encryption [PeerJ] Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key generation and parallel computing for RGB image encryption [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-812/1/fig-1-2x.jpg)